Working from Home Security Challenges / Coronavirus
The bad guys did not waste any time using the Coronavirus pandemic to attack folks who are suddenly Working From Home (WFH) or Studying From Home (SFH). Here is some information to help those of you who are WFH to navigate the perilous path.
Given that many WFH programs were created out of nothing in almost zero time or scaled up from zero to 60, it is no surprise that there might be a security hole or two.
This applies not only to employees working from home but also to students attending school from home.
First of all, hackers are pumping out tons of malicious emails themed around Coronavirus. The malicious emails are compromising systems with password stealing malware and remote access back door software, among other goodies. And don’t forget that old favorite – ransomware. More on that later in this post.
Given how stressed people are, they are likely to forget their security training.
Another challenge for WFH/SFH – making sure that all devices are fully patched. That is going to fall more on the end user now. Companies who have fully automated that are in better shape, but lots of organizations are not set up for that. THIS INCLUDES PHONES AND TABLETS!
Another problem is home and public WiFi. At work, the company can control the setup of company WiFi, but at home it is a bit of the wild west.
For example, when was the last time you patched your WiFi server and your Internet router, modem or firewall?
When did you last have a security expert check the security configuration of those devices?
If your company uses older, in the office systems, they likely do not work very well for remote workers. There is no quick fix for this. It is fixable, but the fix requires new hardware and employee training.
Companies who are in regulated industries such as healthcare, finance or defense have additional problems. How do you continue to comply with the security laws and regulations that these industries have to comply with? In fact, in many of these industries employees are not allow to work remotely by regulation or law.
To make matters worse, in many cases, IT doesn’t have the right tools to securely assist workers who are no longer at the office. If an employee uses a virtual private network (VPN) to connect to their work network, it usually makes it even more difficult for IT to securely connect back to them in order to provide tech support. Even in cases where it does work technically, many times the company has not bought the right support tools to make this possible.
Of course employees who are using their mobile devices more open up yet another attack vector. Many phones and tablets are horribly out of date when it comes to security patches. Many phone manufacturers do a crappy job or releasing patches and for older phones – say more than 2 years old – many times the manufacturer says they are no longer supported and leave the user wide open to a whole raft of attacks.
Companies need to conduct a risk assessment of the remote work environment to make sure that they understand what new risks the company is accepting.
Companies need to consider whether they even have enough security software licenses such as VPN connections. Employees will create unsafe workarounds if the company can’t provide them tools that are secure.
Here is a screenshot of a malicious email. It pretends to be from the CDC, but the email address in the red box shows that this is not the real CDC. The URL in the second red box looks like it is from the CDC, but if you hover over it, it turns out that it is not.

The spam emails might claim to provide information on the Coronavirus or perhaps provide a way for people to contribute to those who need help. Unfortunately, the only one these people are helping are themselves.
KnowBe4 published a picture of an email containing a QR bar code asking for donations (see below). If you want to make the folks in China or North Korea rich, you should donate.

This piece of spam, also from KnowBe4, asks you to watch a Coronavirus video.
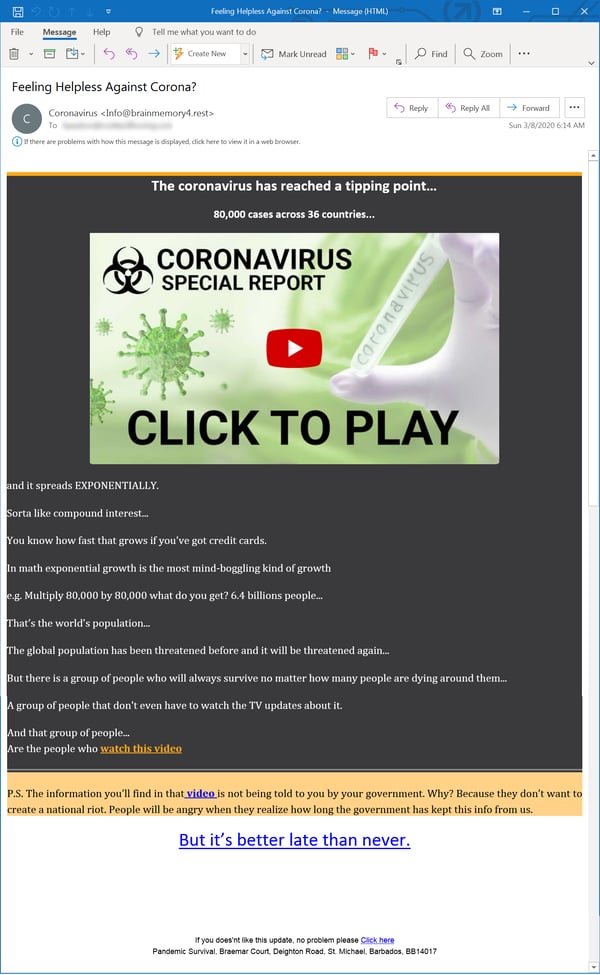
It promises secret information that the government isn’t telling you. If you buy their book for $37.00.
That is actually good because some of them tell you that you need to update your software in order to view this secret video. In fact the update is software that infects your computer, steals your passwords, empties your bank account, encrypts all of your data or some combination of the above.
In the following email, if you just click on the link, some dude will tell you everything you need to know about the Coronavirus and how to stay alive. NOT!
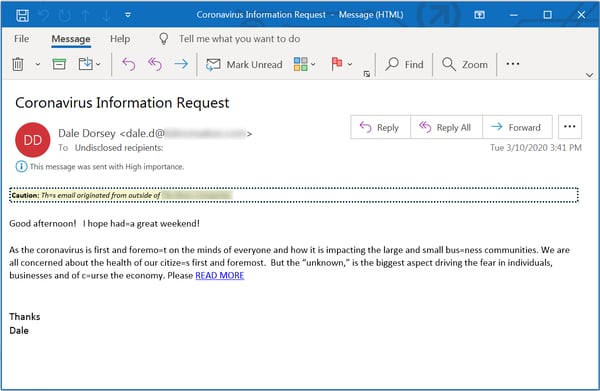
Suffice it to say, this is a bit of a mess and it is not likely to get any better soon.
Companies will, unfortunately in this time of uncertainty, need to up their security spending. The alternative might be a bit of a train wreck.
If you do need help or have security questions. Please reach out to us. After all, we are staying home to stay safe :).
Information for this post came from Threatpost, GCN, the US Secret Service and KnowBe4.
