Ransomware 2.0 Comes of Age
I keep saying that ransomware is morphing; that the ransomware that we have known for the last many years is no more.
It used to be that the hackers could get people to pay by encrypting their data, so people started doing better with backups. Not necessarily great, but better.
So last year one hacker group decided to steal the data that they were encrypting. The technical term is exfiltrate or exfil. It is a bit riskier in that you might be detected sending the data out, but there are a lot of ways to disguise it and if you do it slowly and make it look like all the other data, then you probably won’t get detected. In addition, relatively few companies have any sort of real time alarm system (called a SIEM) in place, again reducing the chance of getting caught.
Up until now, for the most part, the hackers have been THREATENING to release data as a bargaining chip.
Companies are still not paying up, so now one hacking group, REvil, is upping the game. There could be two strategies – one to increase the pressure on companies to pay; the other to make money by selling the data.
Today REvil posted an auction of data from a Canadian Agricultural firm.
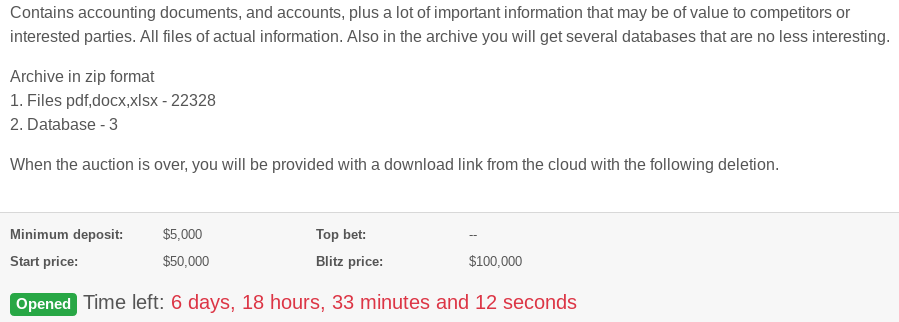
Like many auctions, the bidders have to post a deposit and there is a minimum bid. Very professional.
They say the winner will get 22,000 files and a handful of databases.
What is their plan? Not clear, but they are certainly making victims uncomfortable.
If the data that was stolen was not that sensitive then let them release it. But what if it is sensitive?
Let’s say that they have PII on 10,000 people. In today’s world, not a big catch. Let’s say they are California residents. CCPA says that you can be sued for $750 per person breached without them having to show damage. That would be a $7.5 million upside risk. If the hackers want $100,000, you have to make a business decision.
What if it is national defense data? Or HIPAA data? Or banking data?
The idea of the hackers is to pressure people to pay.
Your mission then is to keep them out. Some things that help are:
Patch: VERY QUICKLY and patch all applications
Disable RDP. Come on. Really. Disable it. No other option.
Filter emails. Likely this means buying a quality email filtering service. If you need help picking one, contact us.
Isolate mission critical systems using micro-segmentation. What the hackers can’t get to, they can’t steal.
Backups, backups and more backups. At least it solves the problem of paying to get your data back.
Disable Office macros. They went dark for a while and now they are coming back as an attack vector.
Enable Windows controlled folder access. This stops hackers from dropping files in certain folders and executing them.
There is no silver bullet, but the objective is to make the hacker’s life difficult. Credit: Brian Krebs
