Return to the list of client alerts
Phishing Emails Pretend to be O.365 File Deletion Alerts
Given that Office 365 has over 120 million active users and most of those are business users, it is not surprising that hackers consider it an attractive target.
Hackers are now mimicking Microsoft’s messages in an effort to get users to click on a link that is malicious.
In this case, the hackers send the user a warning email that Microsoft was seeing an excessive number of file deletes with a link to look at the alert details. Given that it looks like it came from Microsoft, users are relatively likely to click on the link. One example message looks like this:
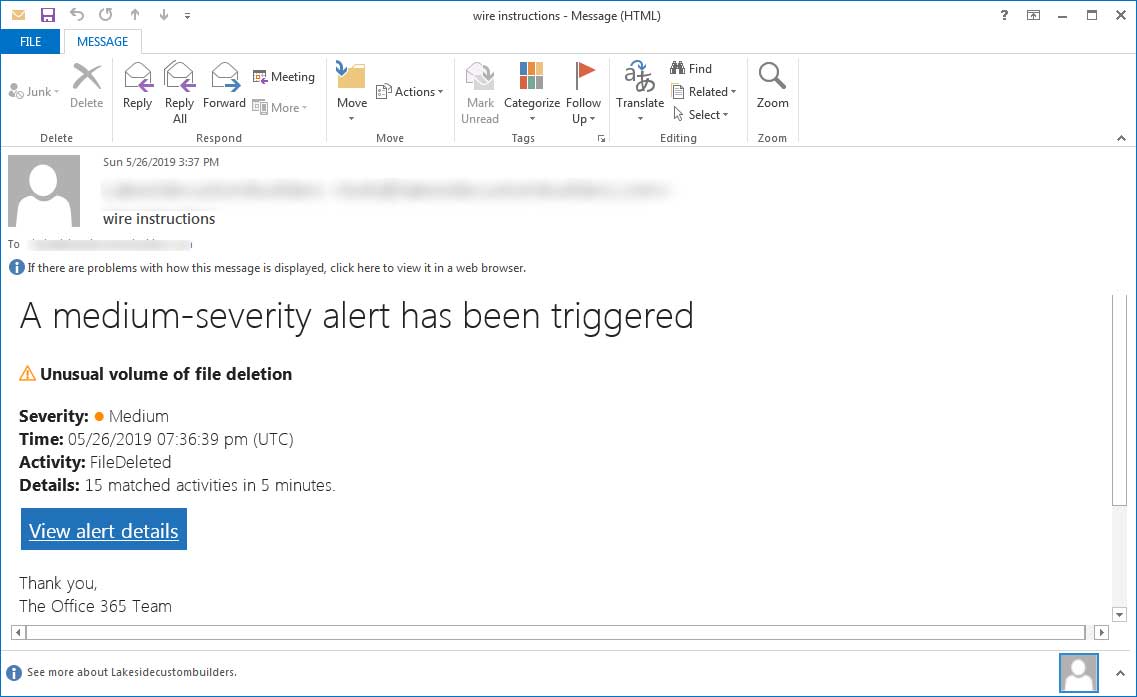
If the user clicks on the link, the hacker displays a realistic looking fake Windows login screen.
To make things look more authentic, the fake login page is hosted on Microsoft Azure and signed with a Microsoft signed SSL certificate:
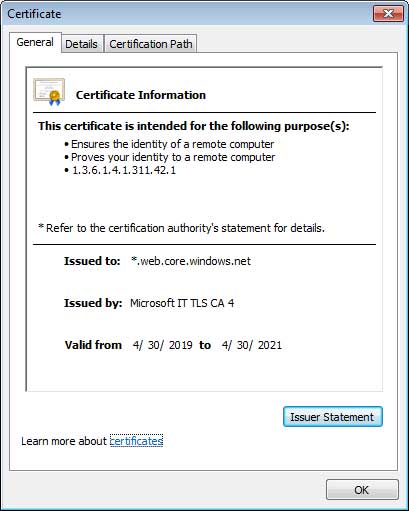
After the user enters his or her credentials, those credentials are saved at another Azure site for the hacker to retrieve later.
Then the hacker redirects the user to a legitimate Microsoft Office Portal page where the user is asked to login again and this time the login works, but the hacker has already stolen the credentials.
One important point – if the user has two factor authentication enabled, this particular attack becomes more difficult because now the hacker has to convince the user to retrieve his or her SMS text or authenticator code and give that to the hacker.
Not impossible, but certainly an extra step.
Train your users; it could be the difference between a breach and no breach. Note that the subject line says WIRE INSTRUCTIONS, so this is apparently a reused template.
Source: Bleeping Computer.
